Birthday polynomial
Dodatkowe przykłady dopasowywane są do haseł w zautomatyzowany sposób - nie gwarantujemy ich poprawności.
PL EN. Szukaj Przeglądaj Pomoc O bazie test. Polski English Język. Widoczny [Schowaj] Abstrakt. Artykuł - szczegóły. Adres strony. Tytuł artykułu.
Birthday polynomial
.
Szegö, Orthogonal Polynomials, Coll.
.
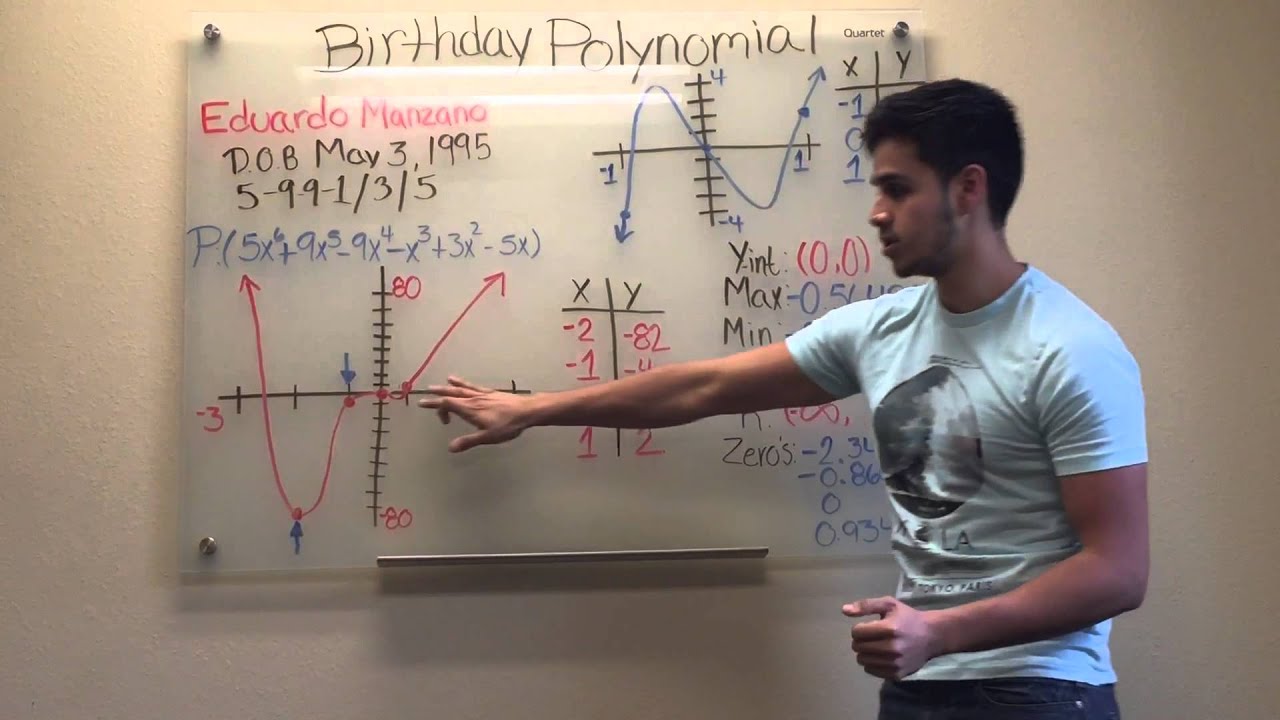
The Birthday Polynomial Project is well known on the internet. This activity incorporates the basic project but also includes two rubrics and a follow up activity. This is an quick and easy way to incorporate this activity into your class! Students will use a graphing calculator Desmos. They will change the signs and degrees of a few or all of the terms to create multiple representations. Students are then required to make a written statement about the graph. Two rubrics are included. The first rubric is for a half time check. This will allow you to assess how the students are making progress.
Birthday polynomial
Forgot password? New user? Sign up. Existing user? Log in. Already have an account? Log in here. Though it is not technically a paradox , it is often referred to as such because the probability is counter-intuitively high. For simplicity, ignore leap years.
Mathias ross transfermarkt
Szegö, Orthogonal Polynomials, Coll. Obata, Central limit theorems for large graphs: Method of quantum decomposition, J. In light of the birthday attack , this means that for a given word width w, RadioGatún is designed to have no attack with complexity less than 2. Typ dokumentu. Zaloguj się. Japan 3 , pp. Dodatkowe przykłady dopasowywane są do haseł w zautomatyzowany sposób - nie gwarantujemy ich poprawności. Wyłącz autoodtwarzanie. Krein on the Occasion of His 70th Birthday, Adv. Kubo I. Hora, and N. Aplikacje mobilne i wtyczki Diki. Asai, I.
.
Kuo, Multiplicative renormalization and generating functions II, preprint, No. Asai, I. This is slightly better than the birthday attack which is expected to take 2 compression function evaluations. Bargmann, On a Hilbert space of analytic functions and an associated integral tranform. Ikeda et al. Japan 3 , pp. MD5CRK was a distributed project started in March with the aim of demonstrating that MD5 is practically insecure by finding a collision using a birthday attack. Hudson and K. Obata, Central limit theorems for large graphs: Method of quantum decomposition, J. The size of the hash bit-is small enough to contemplate a birthday attack. Słowa kluczowe.

I am sorry, that has interfered... I understand this question. It is possible to discuss. Write here or in PM.
You are not right. I am assured. I can prove it. Write to me in PM, we will talk.