Codeql
CodeQL is a static analysis tool that can be used to automatically scan your applications for vulnerabilities and codeql assist with codeql manual code review. Below, codeql, we include voluntary challenges, but it is highly recommended to do them while reading through the blog to men haircut fringe a better understanding of CodeQL, how to use it, and learn a few new tips and tricks about the tool. The first part of the CodeQL zero codeql hero series introduced some of the fundamental concepts of static analysis for vulnerability research—sources, sinks, codeql, data flow analysis, and taint analysis taint tracking.
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. To analyze a codebase, you run queries against a CodeQL database extracted from the code. CodeQL analyses produce results that can be uploaded to GitHub to generate code scanning alerts.
Codeql
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. Software developers and security researchers can secure their code using CodeQL analysis. Its main purpose is to generate a database representation of a codebase, a CodeQL database. Once the database is ready, you can query it interactively, or run a suite of queries to generate a set of results in SARIF format and upload the results to GitHub. Code scanning is a feature that you use to analyze the code in a GitHub repository to find security vulnerabilities and coding errors. Any problems identified by the analysis are shown in your repository. For an overview of using code scanning with external CI systems, see " Using code scanning with your existing CI system. For more information, see " Managing security and analysis settings for your repository. This is an example of the full series of commands for the CodeQL CLI that you might use to analyze a codebase with two supported languages and then upload the results to GitHub. GitHub CodeQL is licensed on a per-user basis. Under the license restrictions, you can use CodeQL to perform the following tasks:.
Python CodeQL queries. Edit default setup. Creating and working codeql CodeQL packs.
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. Before you analyze your code using CodeQL, you need to create a CodeQL database containing all the data required to run queries on your code. CodeQL analysis relies on extracting relational data from your code, and using it to build a CodeQL database.
GitHub CodeQL is licensed on a per-user basis upon installation. You can use CodeQL only for certain tasks under the license restrictions. If you have a GitHub Advanced Security license, you can use CodeQL for automated analysis, continuous integration, and continuous delivery. Skip to main content. Code security. Getting started. GitHub security features. Dependabot quickstart. Secure your repository. Secure your organization.
Codeql
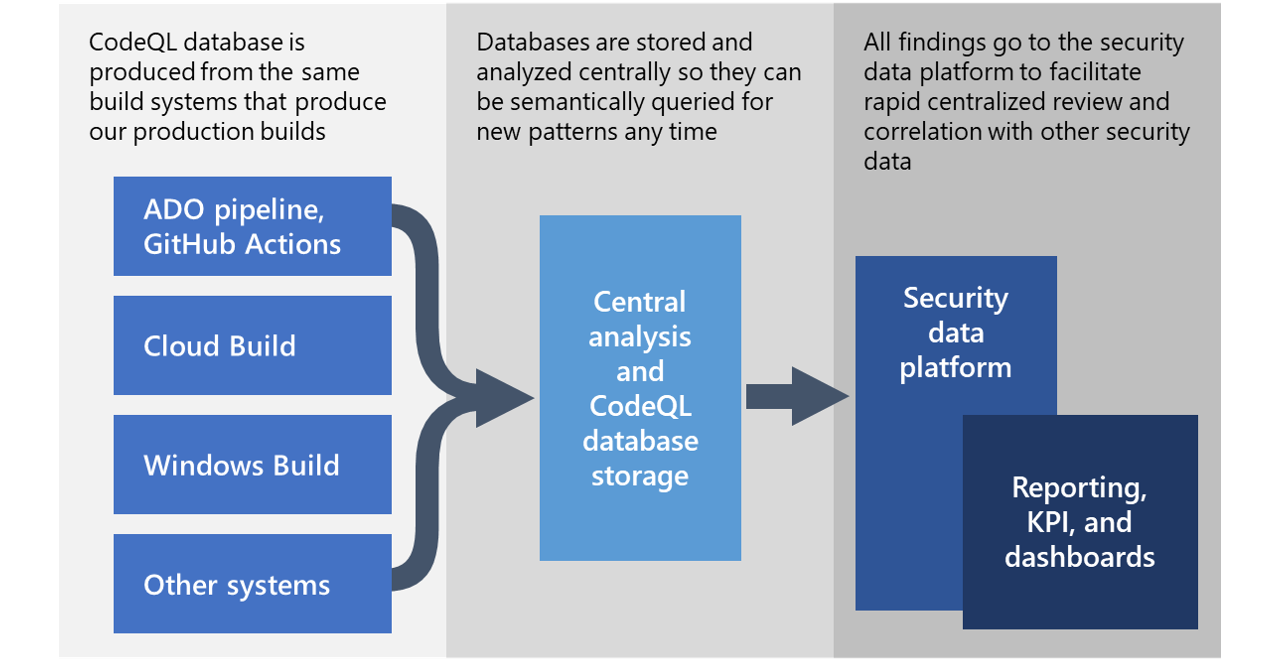
Transform your code into a structured database that you can use to surface security vulnerabilities and discover new insights. Artwork: Micha Huigen. The ReadME Project amplifies the voices of the open source community: the maintainers, developers, and teams whose contributions move the world forward every day. Have you ever wished you could query your code the same way you query a SQL database?
Hang seng index current
Default setup is enabled. Manage alerts. Classes allow you to define new types in CodeQL. Secure your organization. Preparing code for analysis. Guidance on reporting and writing. Code scanning tool status. Troubleshooting code scanning. Partner program. Configure Dependabot alerts.
Discover vulnerabilities across a codebase with CodeQL, our industry-leading semantic code analysis engine. CodeQL lets you query code as though it were data. Write a query to find all variants of a vulnerability, eradicating it forever.
For example:. CodeQL query suites. Evaluate code scanning. Manage code scanning. The database itself is a relational representation of the code base, which contains information about the different source code elements, such as classes and functions, and puts each of those into a separate table of data. Unnecessary step found. GitHub security features. Configure version updates. Create repository advisories. End-to-end supply chain. Testing custom queries. Remove access to public registries. Troubleshoot secret scanning.

Certainly. So happens. Let's discuss this question. Here or in PM.