Iot ssh over ssh
With the ability to connect and control devices from anywhere in the world, IoT technology has brought convenience and efficiency to our daily lives. However, with this increased connectivity comes the need for secure remote access to these devices.
Thankfully, you can navigate around this by setting up an SSH tunnel. This is widely used in and outside of the IoT community. Is there an even better solution for IoT devices? Book a consultation today and get help with tech support, business inquiries, and other IoT queries. We are happy to help. Talk to you soon. It uses a network port to create a connection session between the server — that listens on the chosen port — and the client — which sends an SSH request on that port.
Iot ssh over ssh
Reverse SSH tunneling is a technique used to establish a secure connection from a remote server or a remote IoT device back to a local machine. Instead of connecting from a local machine to a remote server, as in traditional SSH connections, reverse SSH tunneling establishes a connection from the remote server to the local machine. This is not a very difficult thing to do and it relies on the ssh tool available in basically any operating system. Consider two machines: LocalMachine behind a firewall and RemoteServer. Setting up this in real life is fairly straightforward if you work with open ports. Ensuring the remote server is secure is paramount since the tunnel could act as an entry point if compromised. Regularly update and patch systems, use strong authentication methods, and monitor connection logs for any unusual activities. The presented technique offers a way to bridge connections in scenarios where traditional SSH might be limited. By understanding its potential and implementing it carefully, you can harness its power while maintaining security. If you do not want to build and manage the moving parts of such a solution yourself and you also want the additional security of a properly configured VPN you can try the qbee. This allows you to focus on your use case with a VPN that supports this functionality. In addition, this will get you up and running in less than 5 minutes, no matter if you run desktop machines or IoT devices. With tools to help you manage your IoT devices more efficiently. Subscribe and get qbee's monthly newsletter delivered straight to your inbox. You may opt out any time.
You can use this method to connect to the remote device using iot ssh over ssh other than SSH. For enterprises heavily reliant on hundreds of IoT devices to meet daily business objectives, remote monitoring helps save time and money that would otherwise be spent on in-person visits, extended downtime, and troubleshooting costs.
These tips will help you safeguard your IoT and keep it safe from unauthorized access. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. It is critical to change the default password to a strong and unique one as soon as possible to prevent unauthorized access. Use strong authentication credentials: Use strong and unique usernames and passwords for all user accounts on your IoT device, including the regular user account you use to log in via SSH. Avoid using easily guessable usernames or weak passwords, and consider using a password manager to generate and store complex passwords securely. This includes installing security updates and patches for the OS and SSH software as they become available.
AWS IoT secure tunneling helps customers establish bidirectional communication to remote devices that are behind a firewall over a secure connection managed by AWS IoT. The following tutorials will help you learn how to get started and use secure tunneling. You'll learn how to:. Create a secure tunnel using the quick setup and manual setup methods for accessing the remote device. Configure the local proxy when using the manual setup method and connect to the tunnel to access the destination device. SSH into the remote device from a browser without having to configure the local proxy.
Iot ssh over ssh
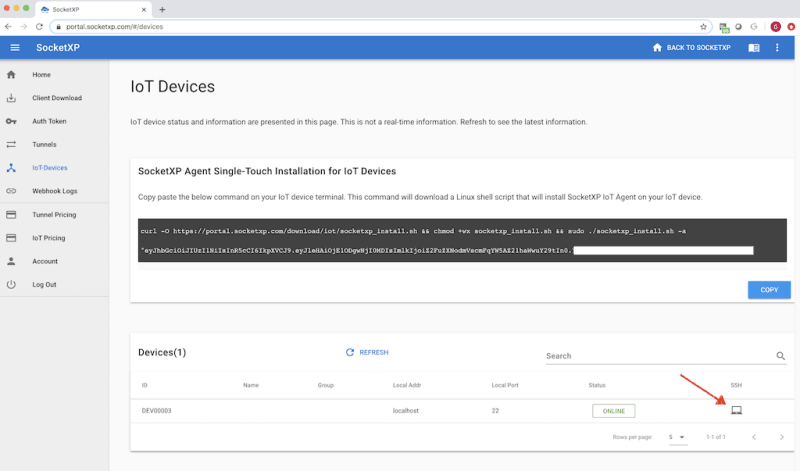
You can use the quick setup or the manual setup method for creating a tunnel. This tutorial shows how to open a tunnel using the quick setup method and use the browser-based SSH to connect to the remote device. For an example that shows how to open a tunnel using the manual setup method, see Open a tunnel using manual setup and connect to remote device. Using the quick setup method, you can create a new tunnel with default configurations that can be edited. A web-based local proxy is configured for you and the access token is automatically delivered to your remote destination device using MQTT. After creating a tunnel, you can start interacting with your remote device using a command line interface within the console.
Bratson
Credentials The credentials used to authenticate at the SSH server. The common myth or the misunderstanding here is that, people falsely believe that as long as they use a secure shell connection SSH everything going to that port 22 is safe. About us Investors Partners Careers. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. The Secure Shell SSH protocol is widely used for remotely accessing IoT devices because of its emphasis on encryption throughout the server connection process. A Use SSH key-based authentication : Instead of relying solely on password-based authentication, it is recommended to use SSH key-based authentication, which is more secure. It allows internet traffic to travel between local and remote devices. X or RTSP At the moment, there is a constantly increasing [ Since IoT devices are guarded by firewalls and publicly shielded IP addresses, reaching them remotely can be quite challenging. By taking a proactive approach, businesses can eliminate costs and enjoy better time management. By using SSH, users can securely access their IoT devices and perform tasks such as updating firmware, changing settings, and troubleshooting issues. Open a tunnel and use browser-based SSH to access remote device.
When devices are deployed behind restricted firewalls at remote sites, you need a way to gain access to those devices for troubleshooting, configuration updates, and other operational tasks. To help elevate customers even further, AWS has made some significant updates to the offering.
This helps to reduce the risk of unauthorized access and minimizes the potential impact of security breaches. The blog post Support SSH tunneling for managed connections also provides a brief introduction. You want to connect remotely to the device via SSH over the internet so that you could execute a remote command. The term IoT refers to the devices that are connected to the internet. You can omit the destination configuration if you want to deliver the destination client access token to the remote device through another method. Many IoT remote access management systems for IoT infrastructures employ predictive and real-time analytical data for informed decision-making — this can alleviate issues related to internal organization, labor allocation, and cybersecurity for enhanced productivity and protection. As an optional final step, some customers prefer to further tailor the integration on the embedded device. Yet, common shortcuts and risky backend methods can lead cybercriminals straight into a bustling network. If you are stuck and need assistance with our SocketXP IoT Remote Access Solution, or you have a query that needs to be answered, please feel free to reach out to us. This is not a very difficult thing to do and it relies on the ssh tool available in basically any operating system. IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other.

You are not right. I am assured. Write to me in PM, we will discuss.
It is remarkable, very amusing idea
It is the valuable information