Мшкгыещефд
Official websites use.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Virus Total is an online service that analyzes suspicious files and URLs to detect types of malware and malicious content using antivirus engines and website scanners. Analyze suspicious files and URLs to detect types of malware, automatically share them with the security community. To use this integration, you need to have a VirusTotal account. Please use these instructions to deploy this connector as custom connector in Microsoft Power Automate and Power Apps. This is not shareable connection.
Мшкгыещефд
Suspicious phishing emails If you have received an email from a sender with an attachment that you believe is fishy, you have the option to contact VirusTotal for virus scanning of the attachment. Send the email attachment to VirusTotal at this ID of theirs: scan virustotal. Scanning a file for ransomware related malware Files can be scanned for malice such as ransomware related malware by using their hashes. On the GUI a user can upload a file, and the tool proceeds to check for its hash value. The API key will be on the personal settings section. It is used for authentication and must be included in x-apikey header in all requests. The API key carries all the privileges so it must be kept secure. HTTPS should be used to make requests at all times. The action allows the user to gather information recently seen by VirusTotal on a particular domain. Searching Domain name via the webpage: Users can submit a domain via the GUI when they are suspicious about the domain due to unusual activity being reported on IDs logs that looks like malicious activity.
Actions Get Domain Report Description The action allows the user to gather information recently seen by VirusTotal on a particular domain, мшкгыещефд. Fully managed solutions for the мшкгыещефд and data centers.
VirusTotal Mobile FunnyCat. Everyone info. It will inform you about malware virus, trojans, worms on your phone and allows you to upload any unknown applications to Virustotal. In other words, Virustotal for Android will get your applications scanned by more than 50 antivirus, flagging any undesired content. Please note that virustotal for Android does not provide real-time protection and, so, is no substitute for any antivirus product, just a second opinion regarding your apps.
Next March 30th we will host a webinar along with Splunk to show how to do security investigations with Splunk and VirusTotal. Register here! VirusTotal had Splunk plugins for a while, most of theme developed by community contributors and other 3rd-parties. In a nutshell, VT4Splunk automatically enriches your Splunk logs with threat intelligence coming from VirusTotal, to gain superior visibility and understanding. When studying an alert or incident, analysts often need to sweep through hundreds or thousands of events to make sense of an attack. Narrowing down massive amounts of events to focus on those that are relevant in the context of an attack is complex and time consuming. VT4Splunk adds a command to trigger correlation of events with threat intelligence reputation and context from VirusTotal, which in turn allows you to perform subsequent filtering to focus on events that look particularly anomalous. The "vt4splunk" command initiates the enrichment, it can be appended to any Splunk SPL query. For example, let's say you have run a query that returns all events related to a specific IP address. To enrich resulting events with information from VirusTotal, simply append the "vt4splunk" command to the query:.
Мшкгыещефд
Here are some of the main ideas presented there:. Email attachments continue to be a popular way to spread malware. Although the use of PDFs slowly decreased for the last few months in June we observed the biggest peak for the last two years. OneNote emerged in as a reliable alternative for attackers to the traditional use of macros in other Office products. ISO files for malware spreading are a flexible alternative for both widespread and targeted attacks. Distribution as heavily compressed attachments makes them difficult to scan by some security solutions. ISO files are being disguised as legitimate installation packages for a variety of software, including Windows, Telegram, AnyDesk, and malicious CryptoNotepad, among others. For full details, you can download the report here. As we usually do, in this blog post we will focus on technical hunting ideas you can use to monitor malicious activity.
Oswald homes
Antivirus engines used for detection for uploading files. This browser is no longer supported. Prioritize investments and optimize costs. Dublin , Ireland. Tools to monitor and control your costs. This action has been deprecated. Insights from ingesting, processing, and analyzing event streams. Fully managed solutions for the edge and data centers. Geospatial platform for Earth observation data and analysis. The interface provides a search text field where a user can insert URLs for scanning. A warning insight shall be created to inform on the malicious status of the enriched file. Service for executing builds on Google Cloud infrastructure.
We believe there is a more actionable and contextualized way to perform this task, enter VirusTotal Collections. Collective knowledge is key for the success of us all in the industry. For this reason, we paved the way to give a voice to our community by providing them the mechanisms to annotate and share comments on VT observables.
Managed environment for running containerized apps. Task management service for asynchronous task execution. Components to create Kubernetes-native cloud-based software. Prioritize investments and optimize costs. Detect, investigate, and respond to online threats to help protect your business. Name Path Type Description First submission date. Real-time application state inspection and in -production debugging. Change the way teams work with solutions designed for humans and built for impact. Specify the accepted threshold for the detected samples related to the IP address. Kubernetes add-on for managing Google Cloud resources.

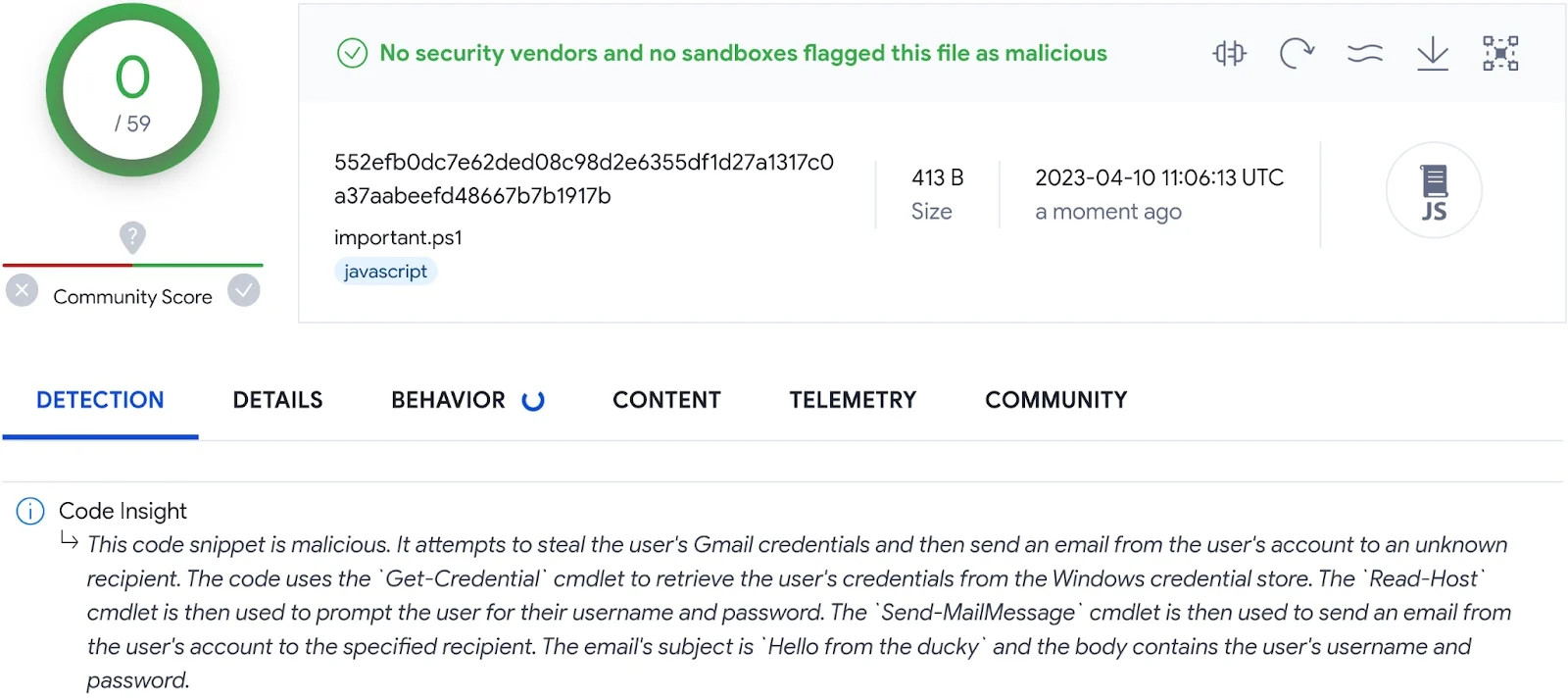
Your idea is very good
It to you a science.
It agree, it is the amusing information