Slam acronym cyber security
Protecting your company from cyber threats can take a lot of different forms.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organisations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences. Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security.
Slam acronym cyber security
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less! Remember having to download pop-up blockers and Norton Antivirus software or having your computer crash? Transitioning to cloud-based infrastructures created a cornucopia of critical failure points and security gaps. Not only does this cost billions, but it creates a deadly ripple effect reputationally and legally and can threaten human life in the healthcare setting. While many would argue that cyberattacks can be blamed on one failed password or misconfiguration, hacking happens in stages, making it critical to be vigilant. This article will define some key terms, explain types of email phishing, describe the SLAM method, and provide examples of how to protect yourself. There are four key players in this cyber world:. A large meta-analysis in looked at 70 articles published in the last 12 years on cybersecurity. While several security gaps made the headlines, phishing rose to the top. Email phishing is an online scam where cybercriminals send emails designed to appear as if they are from legitimate sources to trick people into giving out their personal information, such as bank account numbers, passwords, or credit card numbers. The emails often appear to be from well-known organizations, such as banks or tech companies and contain links that direct users to malicious websites or to download malicious software.
The way the data breach was caught?
Phishing is a type of cyber attack that involves tricking someone into giving up sensitive information, such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer. Cybercriminals typically use email as the primary attack vector. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security. As mentioned in the intro of this article, this will be a short and sweet explanation of what SLAM is and how your business can implement it. I receive a spear-phishing attempt once a week.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organizations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences.
Slam acronym cyber security
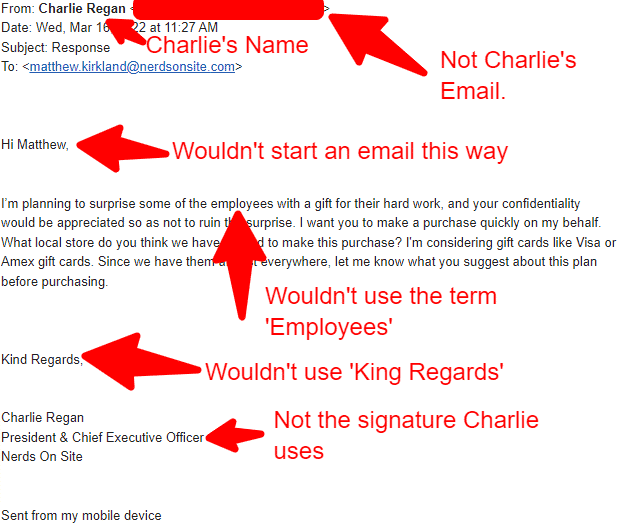
Please support Telehealth. Phishing attacks have been targeting healthcare organizations with a vengeance. An example of such malicious software is ransomware. Fortunately, there is a simple acronym that can be used to quickly remember the important steps to identify phishing attacks as they enter your inbox. SLAM is an acronym that stands for a review that involves double-checking the sender, link, attachment, and message before clicking anything in the email that might deploy a download. They often involve an offer for free or dramatically discounted services or benefits from a large, respected organization. The SLAM acronym serves as a reminder of what to determine whether or not an email is fraudulent and can hurt your computer or its infrastructure.
100000 yen to usd
I receive a spear-phishing attempt once a week. Report the phishing attempt to your IT department so they can blacklist the domain address of the sender. It has likely fooled many people into divulging their personal details. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful. Especially in the work environment, where we have hundreds of things to process. If you want to know more about social engineering attacks on businesses and have 7 minutes, you should watch the following video of Rachel Tobac, CEO of SocialProof Security. Spear Phishing - This attack is more targeted than deceptive phishing and is tailored to a specific group or individual. If the answer to any of these questions is no, it is best practice to pick up that phone or walk down the hall to verify the email is legitimate. This along with a court order to pay back the rest of the stolen money. Why has phishing remained such a large threat for so long?
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less! Remember having to download pop-up blockers and Norton Antivirus software or having your computer crash?
Report the email to your management team so they can alert the company. Our Product. Emails from cybercriminals can look just like any ordinary email you might receive. What is a Cyber Security Framework? It helps us quickly process a lot of incoming information each day. While phishing emails have become more sophisticated over the years, the content of the message itself can often be a dead giveaway. This website uses Google Analytics which collect anonymous information such as the number of visitors to the site, and the most popular pages. Get in touch. Increasing Efficiency. An email coming from Microsoft support would read [email protected]. With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up? Some notable examples include: Monitoring and securing public Wi-Fi networks in retail establishments, airports, and other public spaces. This is because HIPAA Security Rule requirements set a minimum standard for implementing safeguards to ensure the confidentiality, integrity, and availability of protected health information PHI.

0 thoughts on “Slam acronym cyber security”