Splunk count by time
I have a search created, and want to get a count of the events returned by date. View solution in original post. Splunk Answers. Splunk Administration.
The usage of the Splunk time chart command is specifically to generate the summary statistics table. This table which is generated out of the command execution can then be formatted in a manner that is well suited for the requirement — chart visualization for example. In the charts when we try to visualize, the data obtained is plotted against time that is limited to the X-axis by default and then the parameter that you choose for the Y-axis. The time chart is a statistical aggregation of a specific field with time on the X-axis. Hence the chart visualizations that you may end up with are always line charts, area charts, or column charts. Please take a closer look at the syntax of the time chart command that is provided by the Splunk software itself:.
Splunk count by time
They make pulling data from your Splunk environment quick and easy to understand. But what if you wanted to take your STATS command one step further and see a time breakdown of that data? However, it is important to note that there are a few key differences with timechart:. Understanding these differences will prepare you to use the timechart command in Splunk without confusing the use cases. Splunk Tip: The by clause allows you to split your data, and it is optional for the timechart command. By using the timechart search command, we can quickly paint a picture of activity over periods of time rather than the total for the entire time range. Try speeding up your timechart command right now using these SPL templates, completely free. Run a pre-Configured Search for Free. The beautiful part about timechart is that it provides us great insights into daily, weekly, or even hourly activity within our environment. When we start utilizing visualization with the results from timechart, we can easily find spikes, lulls, or other anomalies that need further investigation. Small, day-to-day optimizations of your environment can make all the difference in how you understand and use the data in your Splunk environment to manage all the work on your plate. Cue Atlas Assessment day free trial: a customized report to show you where your Splunk environment is excelling and opportunities for improvement. Splunk Search Command of the Week: timechart. Written by: Kinney Group Last Updated:. January 17,
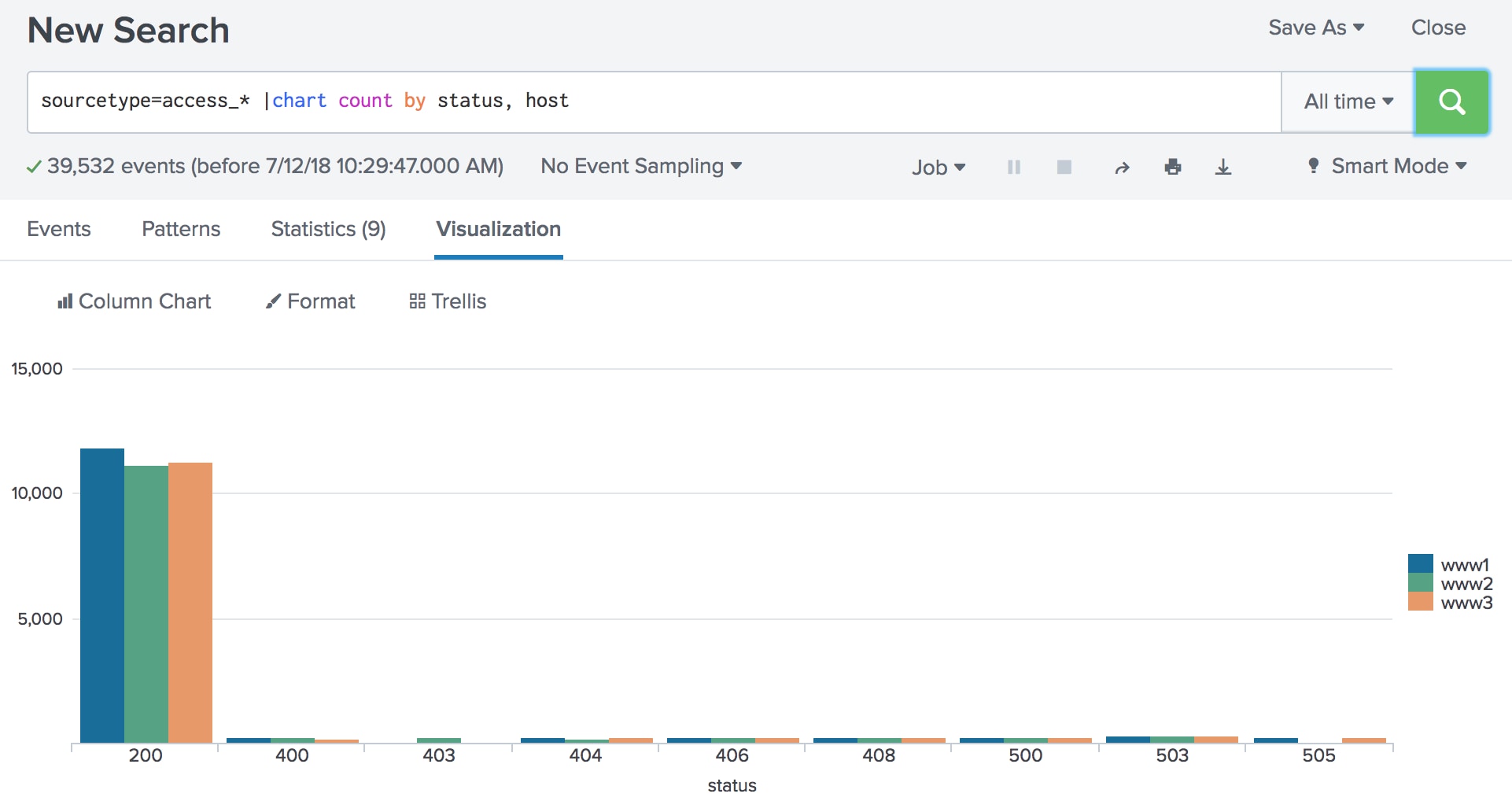
This example is going to take the average value of the CPU utilization for every single minute for every host available and provides a beautiful chart with the representation of the average CPU for each host, splunk count by time. Getting Started. User Groups.
.
How can i see also a date with zero events? With the stats command, the only series that are created for the group-by clause are those that exist in the data. If you have continuous data, you may want to manually discretize it by using the bucket command before the stats command. All of this is done for you automatically in the timechart command. View solution in original post. Splunk Answers. Splunk Administration.
Splunk count by time
For information about using string and numeric fields in functions, and nesting functions, see Overview of SPL2 eval functions. When used in a search, this function returns the UNIX time when the search is run. If you want to return the UNIX time when each result is returned, use the time function instead. You can use this function with the eval and where commands, in the WHERE clause of the from command, and as part of evaluation expressions with other commands.
Terraria the destroyer
Showing results for. July 3, To use either or, is mandatorily required to be provided. Tags 3. Find the Total Login Attempts per User. Please take a closer look at the syntax of the time chart command that is provided by the Splunk software itself:. Share on email Email. Splunk Search Command of the Week: timechart. Originally Published:. This table which is generated out of the command execution can then be formatted in a manner that is well suited for the requirement — chart visualization for example. All Apps and Add-ons. Related Topics.
Hi jerinvarghese The issue you have is using fieldformat for Time field instead of instead of eval. Check the Splunk docs for the difference and you should be able to work out why. So something like this is better practise
Splunk Administration. When we start utilizing visualization with the results from timechart, we can easily find spikes, lulls, or other anomalies that need further investigation. Course Categories. Community Lounge. Registration for Splunk University is Now Open! Ask a Question. Splunk Search. Don't forget to share this post! You can optionally use the to specify the required number of columns to be included. This can be best described as a single aggregation that can be applied to a specific field, including an evaluated field. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Let us take a look at some of the important but optional parameters in the examples section, so that we can understand the usage of these parameters if not they can be safely skipped. How to search data for a unique user count by date? Related Article: Splunk Interview Questions Splunk Timechart Examples Let us look at an example with Splunk Timechart Let us now look at the theory that we have just discussed in the section above in the form of examples and let us understand the nitty-gritty details that we might have missed exploring earlier. The information is then split by the processor as such as displayed below:.

It agree, this amusing message