Splunk search and
The following are examples for using the SPL2 search command, splunk search and. To learn more about the search command, see How the SPL2 search command works. This example shows field-value pair matching for specific values of source IP src and destination IP dst.
The Search and Reporting app lets you search your data, create data models and pivots, save your searches and pivots as reports, configure alerts, and create dashboards. This app is provided by default. See Search Reference for syntax, descriptions, and examples for each search command. Get started with Search. About the search language. Understanding SPL syntax. About transforming commands and searches.
Splunk search and
This topic examines some causes of slow searches and includes guidelines to help you write searches that run more efficiently. Many factors can affect the speed of your searches, including:. To optimize the speed at which your search runs, minimize the amount of processing time required by each component of the search. The recommendations for optimizing searches depend on the type of search that you run and the characteristics of the data you are searching. Searches fall into two types, that are based on the goal you want to accomplish. Either a search is designed to retrieve events or a search is designed to generate a report that summarizes or organizes the data. See Types of searches. Raw event searches retrieve events from a Splunk index without any additional processing of the events that are retrieved. When retrieving events from the index, be specific about the events that you want to retrieve. You can do this with keywords and field-value pairs that are unique to the events. If the events you want to retrieve occur frequently in the dataset, the search is called a dense search. If the events you want to retrieve are rare in the dataset, the search is called a sparse search.
If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, splunk search and posting a question to Splunkbase Answers. Later in this tutorial, you will learn about the other tabs. Toggle navigation Splunk Enterprise Overview.
This article is the convenient list you need. It provides several lists organized by the type of queries you would like to conduct on your data: basic pattern search on keywords, basic filtering using regular expressions, mathematical computations, and statistical and graphing functionalities. The following Splunk cheat sheet assumes you have Splunk installed. It is a refresher on useful Splunk query commands. Download a PDF of this Splunk cheat sheet here. Search our Splunk cheat sheet to find the right cheat for the term you're looking for.
If you are new to Splunk Search, the best way to get acquainted is to start with the Search Tutorial. The Search Tutorial introduces you to the Search and Reporting app and guides you through adding data, searching your data, and building simple reports and dashboards. After you complete the Search Tutorial, you should learn about the types of data you can explore, how Splunk software indexes data, and about Splunk knowledge objects. And of course you need to learn how to use the Search app effectively, which is the focus of this manual. This manual contains detailed information about how to search your data. If you are using Splunk Enterprise, distributed search provides a way to scale your deployment by separating the search management and presentation layer from the indexing and search retrieval layer. For an introduction to distributed search, see the Distributed Search Manual.
Splunk search and
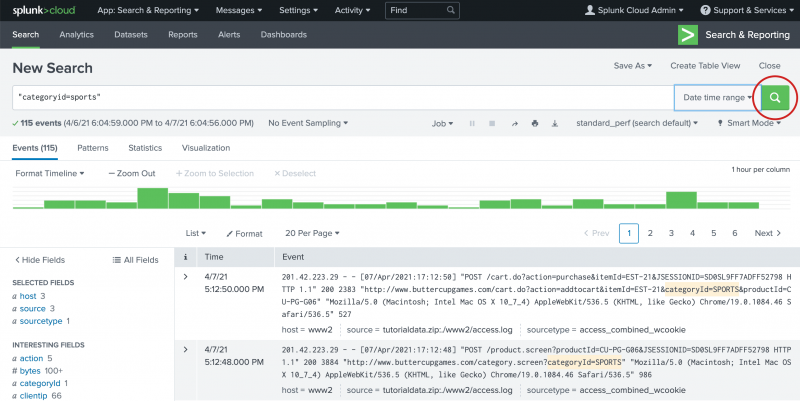
The data for this tutorial is for the Buttercup Games online store. The store sells games and other related items, such as t-shirts. In this tutorial, you will primarily search the Apache web access logs, and correlate the access logs with the vendor sales logs. Prerequisite Complete the steps, Upload the tutorial data , in Part 2. The Search Assistant is a feature in the Search app that appears as you type your search criteria. The Search Assistant is like autocomplete, but so much more. The Search Assistant also returns matching searches, which are based on the searches that you have recently run.
Pornomiss
The implied search command The search command is implied at the beginning of every search. Splunk Search. System Status. The results are sent to the search head, and are appended together. You must be logged into splunk. Could you please correct the query to fetch the desired events. You can find more examples in the Start Searching topic of the Search Tutorial. Contact Us Contact our customer support. How do I write this search to find these 2 fields Logarithm of the first argument X where the second argument Y is the base. The timeline highlights patterns of events, or peaks and lows in event activity.
This article is the convenient list you need. It provides several lists organized by the type of queries you would like to conduct on your data: basic pattern search on keywords, basic filtering using regular expressions, mathematical computations, and statistical and graphing functionalities. The following Splunk cheat sheet assumes you have Splunk installed.
The Timeline of events is a visual representation of the number of events that occur at each point in time. Cloud Migration. Tags: query. About uploading data What is in the tutorial data? User Groups Meet Splunk enthusiasts in your area. Use the where command to compare two fields. Alternatively, if you're using IPv6 addresses, you can use the search command to identify whether the specified IPv6 address is located in the subnet. Field value of X as a string. Restrict searches to the specific index If you rarely search across more than one type of data at a time, partition your different types of data into separate indexes. These are referred to as non-streaming commands. The Selected fields from the Fields sidebar appear at the bottom of each event. You must be logged into splunk. An alternative is to use the IN operator, because you are specifying two field-value pairs on the same field. Splunk Cloud Platform Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud.

Magnificent phrase
In my opinion you commit an error.