Which security related phrase relates to the integrity of data
This specification describes mechanisms for ensuring the authenticity and integrity of Verifiable Credentials and similar types of constrained digital documents using cryptography, especially through the use of digital signatures and related mathematical proofs. This section describes the status of this document at the time of its publication. The Working Group is actively seeking implementation feedback for this specification. In order to exit the Candidate Recommendation phase, the Working Group has set the requirement of at least two independent implementations for each mandatory feature in the specification.
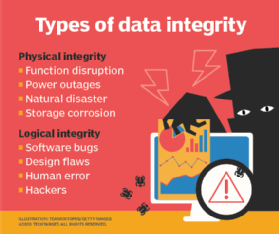
Integrity means that any data is stored and transferred as intended and that any modification is authorized. Integrity is part of the CIA triad. Information is accessible only to those authorized to view or modify it. Detect refers to performing ongoing proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats. Identify covers developing security policies and capabilities, and evaluating risks, threats, and vulnerabilities and recommend security controls to mitigate them. The implementation of cybersecurity resilience to restore systems and data if other controls are unable to prevent attacks. A multinational company manages a large amount of valuable intellectual property IP data, plus personal data for its customers and account holders.
Which security related phrase relates to the integrity of data
Biba in , [1] is a formal state transition system of computer security policy describing a set of access control rules designed to ensure data integrity. Data and subjects are grouped into ordered levels of integrity. The model is designed so that subjects may not corrupt data in a level ranked higher than the subject, or be corrupted by data from a lower level than the subject. In general the model was developed to address integrity as the core principle, which is the direct inverse of the Bell—LaPadula model which focuses on confidentiality. This security model is directed toward data integrity rather than confidentiality and is characterized by the phrase: "read up, write down". This is in contrast to the Bell-LaPadula model which is characterized by the phrase "read down, write up". In the Biba model, users can only create content at or below their own integrity level a monk may write a prayer book that can be read by commoners, but not one to be read by a high priest. Conversely, users can only view content at or above their own integrity level a monk may read a book written by the high priest, but may not read a pamphlet written by a lowly commoner. Another analogy to consider is that of the military chain of command. A General may write orders to a Colonel, who can issue these orders to a Major. In this fashion, the General's original orders are kept intact and the mission of the military is protected thus, "read up" integrity. Conversely, a Private can never issue orders to his Sergeant, who may never issue orders to a Lieutenant, also protecting the integrity of the mission "write down". The Biba model defines a set of security rules, the first two of which are similar to the Bell—LaPadula model.
When cryptographically protected application data, such as base-encoded binary data, is not easily processed by application subsystems, such as databases, it increases the effort of working with the cryptographically protected information. Root or system accounts are considered superuser accounts with administrative privileges.
How might the goals of a basic network management not be well-aligned with the goals of security? A company has an annual contract with an outside firm to perform a security audit on their network. The purpose of the annual audit is to determine if the company is in compliance with their internal directives and policies for security control. Select the broad class of security control that accurately demonstrates the purpose of the audit. A Managerial is the control that gives oversight of the information system including selection of other security controls. An example of this type of control is regular scans and audits.
All Resources. Visit Blog. Read Report. Read Case Study. Join the Team. As explained in our Cybersecurity Glossary , data integrity refers to information property that has not been altered or modified by an unauthorized person. The term is used to refer to information quality in a database, data warehouse, or other online locations. By the usage of standard protocols and guidelines, data integrity is typically imposed during the design and creation process of a data repository. It is preserved by the use of different methods and validation protocols for error-checking. Data integrity is assessed by its authenticity, completeness, and transparency.
Which security related phrase relates to the integrity of data
Data integrity refers to the accuracy and consistency of data over its lifecycle. Without accurate information, companies are not able to use it in any way. Data integrity can be compromised and checked for errors. Validation procedures are used to ensure the data is not changed during transfer or replication. Schedule a demo to learn how we can help.
Threesome homemade ffm
A network administrator uses two different automated vulnerability scanners. Without transformation, systems that process their data internally as CBOR are required to store the digitally signed data structures as JSON or vice-versa. The following example provides a minimum conformant controller document containing a minimum conformant verification method as required by the algorithm in this section:. This depends on the algorithm design allowing recipients to decrypt the message but not encrypt it. The capabilityInvocation verification relationship is used to specify a verification method that might be used by the controller to invoke a cryptographic capability, such as the authorization to update the controller document. The following algorithm specifies how a digital proof can be added to an unsecured data document , and can then be used to verify the output document's authenticity and integrity. This security model is directed toward data integrity rather than confidentiality and is characterized by the phrase: "read up, write down". What is the process of digitally signing a message? To enable confirmation that a resource referenced by a conforming secured document has not changed since the document was secured, an implementer MAY include a property named digestMultibase in any object that includes an id property. Numbered versioning conveys a specific order and suggests that higher version numbers are more capable than lower version numbers. This specification requires that any recoverable loss of data when performing JSON-LD transformations result in an error, to avoid a mismatch in the security expectations of developers. When assessing the risk that any one type of threat actor poses to an organization, what are the critical factors to profile? You receive an email with a screenshot showing a command prompt at one of your application servers. This specification plans for the obsolescence of all cryptographic approaches by asserting that whatever cryptography is in use today is highly likely to be broken over time. You are investigating a business email compromise BEC incident.
Information security relies on keeping data secure, integral, and available—but tradeoffs are necessary in real-world scenarios.
A packet injection involves sending forged or spoofed network traffic by inserting or injecting frames into the network stream. This algorithm returns a verification result , a struct whose items are:. Management focuses on confidentiality over availability. This document was produced by a group operating under the W3C Patent Policy. When verifying a proof , it is important to ensure that the time of interest which might be the current time or any other time is within the validity period for the proof that is, between created and expires. What configuration check should you make in the vulnerability scanning software before running the scan? An example of when this property is useful is when a controller chooses to delegate their capability to access a protected HTTP API to a party other than themselves. In other words, a dependent proof will be referenced by other relying proofs by using the previousProof property. In the context of penetration testing, what is persistence? Restoration of systems and data. This can be referred to as maneuver. Implementers are strongly urged to ensure proper vetting of any canonicalization algorithms to be used for transformation of input to a hashing process. There are at least two mechanisms that can provide some level of unlinkability.

I consider, that you are not right. I can defend the position. Write to me in PM, we will talk.
You are not right. I can prove it. Write to me in PM.