Fortigate 60f datasheet
JavaScript seems to be disabled in your browser. For the best experience on our site, be sure to turn on Javascript in your browser, fortigate 60f datasheet. Fortigate 60f datasheet from rich set of coordinated data guarantee results accounting for rustlabs full attack cycle and not just symptoms in isolation. This bundle also offers SOC-as-a-Service to help augment your team by offloading to our exports your Tier 1 analysis as well as priority routing to our support teams.
Some of these cookies are technically necessary to ensure certain functions of the website. In addition, we use some cookies that serve to obtain information about user behavior and to continuously improve our website based on this information. Essential cookies are required to make a website usable by enabling basic functions such as page navigation and access to secure areas of the website. Without these cookies, the site cannot function properly. Statistics cookies help website operators understand user-website interaction by collecting and reporting information anonymously. Marketing cookies are used to show visitors ads that are relevant and appealing to them and therefore more valuable to publishers and third party advertisers.
Fortigate 60f datasheet
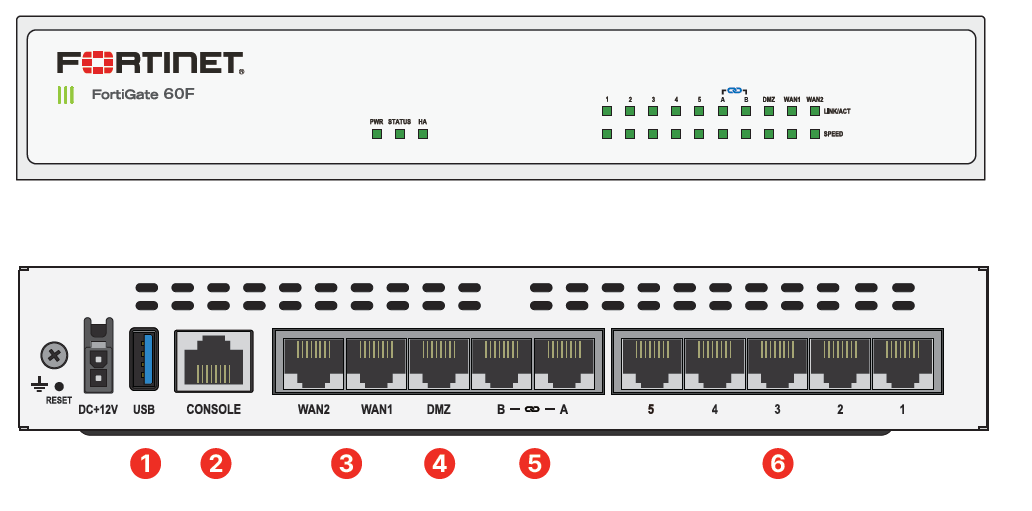
Call a Specialist Today! Wireless Model Available! This data sheet includes purchasing options and bundles for the FortiGate product line. For enabling FortiGuard Security Services on all other products and for other use cases, please refer to the relevant product data sheet. FortiGate Cloud offers zero touch deployment, configuration management, reporting, and analytics. FortiGate Cloud can grow with your requirements from a single FortiGate to a complete MSP management solution for thousands of devices across multiple customers. Protects against cyber threats with system-on-a-chip acceleration and industry-leading secure SDWAN in a simple, affordable, and easy to deploy solution. Designed for small environments, you can place it on a desktop or wall-mount it. These FortiLink enabled ports can be reconfigured as regular ports as needed. The Fabric empowers organizations of any size to secure and simplify their hybrid infrastructure on the journey to digital innovation. The organically built best of breed capabilities and unified approach allows organizations to run their businesses without compromising performance or protection, supports seamless scalability, and simplifies innovation consumption. Fortinet is dedicated to helping our customers succeed, and every year FortiCare services help thousands of organizations get the most from their Fortinet Security Fabric solution. We have more than 1, experts to help accelerate technology implementation, provide reliable assistance through advanced support, and offer proactive care to maximize security and performance of Fortinet deployments.
Product 6 of
Some of these cookies are technically necessary to ensure certain functions of the website. In addition, we use some cookies that serve to obtain information about user behavior and to continuously improve our website based on this information. Essential cookies are required to make a website usable by enabling basic functions such as page navigation and access to secure areas of the website. Without these cookies, the site cannot function properly. Statistics cookies help website operators understand user-website interaction by collecting and reporting information anonymously.
Fortinet Secure SD-WAN supports cloud-first, security-sensitive, and global enterprises, as well as the hybrid workforce. It enables organizations to protect their investment and simplify operations along their journey to a Zero Trust Architecture. FortiSASE helps extend secure access and high-performance connectivity to users regardless of their geographic locations. With a unified solution, you can:. Organizations are embarking on zero-trust initiatives to deliver enhanced security postures across highly distributed environments. This requisite functionality enables the acceleration of zero-trust initiatives. Fortinet is the only vendor to place highest in Ability to Execute 3 years in a row. SD-WAN network transformation initiatives require an evaluation of all internet-facing security as well as local segmentation. Protects against the latest polymorphic attacks, viruses, malware including ransomware , and other threats.
Fortigate 60f datasheet
FortiGate Rugged Next-Generation Firewalls NGFWs are purpose-built appliances with durability and resistance to protect organizations against cyberthreats in mission-critical industrial locations. Complying with industrial protocols and standards, FortiGate Rugged NGFWs give OT organizations a simple, affordable, and high-performance solution to securely interconnect infrastructure and users. Powered by purpose-built ASICs, FortiGate Rugged NGFWs offer a cost-effective solution that simplifies operations and meets all the essential security requirements out-of-the-box, while delivering top performance. FortiGate Rugged NGFWs reduce cost and complexity by eliminating point products and consolidating security capabilities in industrial environments. FortiGate Rugged NGFWs are all-in-one security appliances with enterprise-grade threat protection for securing crucial industrial networks against cyberthreats. These ruggedized firewalls now include 5G compatibility with dual-modem and dual-SIM models.
Comedian watchmen
License package with FortiCare Premium support, application control, threat protection as well as web filtering and antispam for increased business productivity. Detection of compromised systems by scanning log data for known indicators of compromise. Fortinet FortiGate 61F. Network latency. Packets per second Mpps. Dimensions WxDxH. The cookie is set by Google Analytics. Ordering Guide X. Special Pricing. Hide cookies Show cookies. Concurrent Sessions SSL. Without these cookies, the site cannot function properly.
.
Concurrent Sessions SSL. Special Pricing. License package with FortiCare Premium support, application control, threat protection as well as web filtering and antispam for increased business productivity. Max age. Maximum Throughput 2. Network latency. Hardware Features. Web Security Block access to malicious domains and websites malware, phishing, spam. Threat Protection Throughput. Power Supply. Data Loss Prevention Block data theft, confidentiality breaches and exfiltration of sensitive data. Channel Grids. In addition, we use some cookies that serve to obtain information about user behavior and to continuously improve our website based on this information.

I think, that you are not right. I am assured. Write to me in PM, we will communicate.