How to access /etc/shadow file without root
Connect and share knowledge within a single location that is structured and easy to search.
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information.
How to access /etc/shadow file without root
It has been a while since I worked on anything PAM related, but I recently became interested in exploring how to convert the su binary to work with capabilities only, and not require it being setuid-root. Recall, in this environment , being root comes with no super user privilege. However, we shouldn't ever forget that root owns a lot of system files! That was a set of applications those of us, that originally developed Linux-PAM, wrote to prototype modules and libpam improvements against. I had a prototyping project related to libcap now and, while a couple of decades had elapsed, it was fun to take that code out for a spin again. Which is what we actually need to have su correctly function. In PURE1E mode the su program won't be running as setuid-root , but we want the code to authenticate other users So, that code needed to change. Next up rewriting some version of su to have no requirement to be run-as- root. Bootstrapping acceptance of its abstraction and validating that modules were compatible by design vs. They were useful for development purposes, but were never adopted as actual replacements for system tools, instead, folk modified the standard tools to support PAM abstractions. However, since I had some memory of working with that code, I decided to refactor the version of su from that tar ball. As was the case with the SimplePAMApps , we don't expect this binary to become standard on any distribution but, we're happy to receive bug reports and or patch fixes against it.
Improve this answer. Why do you believe that it's not? Please add further details to expand on your answer, such as working code or documentation citations.
Connect and share knowledge within a single location that is structured and easy to search. I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. They can't copy it, open it; etc. Is there some brute force method? I don't know anything about these, where can I learn? In order to understand how a hacker could access this file you have to think like a hacker, mainly outside the box, of what most would consider to be "normal" methods for accessing a file. I've seen many examples throughout my career where developers or unknowledgeable sysadmins have run applications such as Tomcat or Apache as root.
Ask questions, find answers and collaborate at work with Stack Overflow for Teams. Explore Teams. Connect and share knowledge within a single location that is structured and easy to search. I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. They can't copy it, open it; etc. Is there some brute force method? I don't know anything about these, where can I learn? In order to understand how a hacker could access this file you have to think like a hacker, mainly outside the box, of what most would consider to be "normal" methods for accessing a file. I've seen many examples throughout my career where developers or unknowledgeable sysadmins have run applications such as Tomcat or Apache as root. These same methods can be used to augment the permissions on files as well, though a good hacker would not do something so obvious as to be detected, safer to read the contents of these files and stash them somewhere else or retrieve them from the box.
How to access /etc/shadow file without root
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information.
Surrounded by crossword
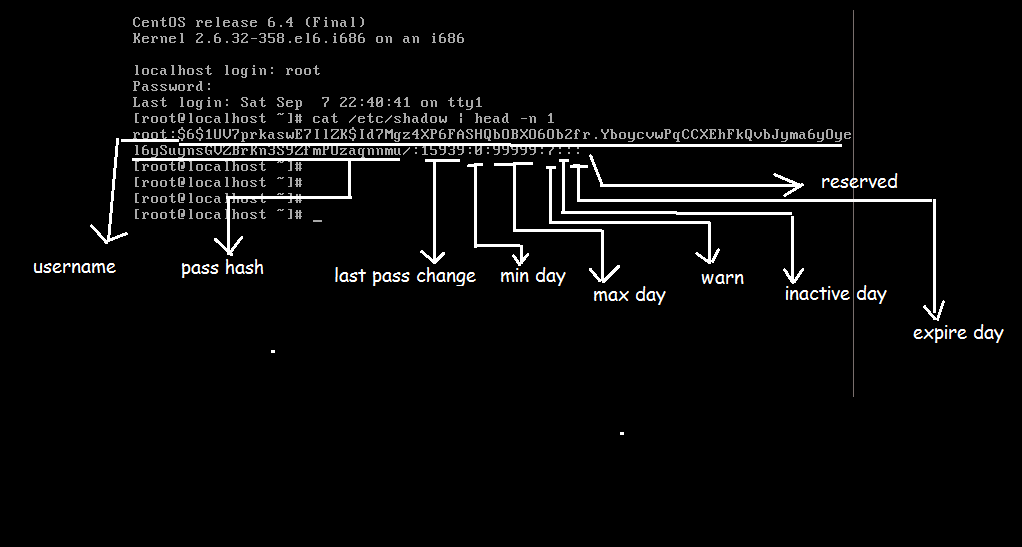
If the value is set to 0 zero , user is allowed to change his password immediately. I don't know anything about these, where can I learn? If two or more users have selected the same password, due to this feature, their encrypted passwords will be different. If you want that feature, you can also use a more traditional, but actually Linux-PAM compliant , setuid-root version of su. But the issue is that, if a hacker manages to gain root access by exploiting a system vulnerability, you don't want them to be able to simply read the passwords. This configuration is intended to support only the privilege that su needs to do its work, and the source code can be audited with this in mind. Sorted by: Reset to default. Question feed. Connect and share knowledge within a single location that is structured and easy to search. Changing an owner group of such important file could even break some things, which is dangerous. However, we shouldn't ever forget that root owns a lot of system files!
.
Connect and share knowledge within a single location that is structured and easy to search. For example, to set account expiration date to 28 June , number will be used. Systemd Units Explained with Types and States. If you are interested in learning how to enable the root account in Ubuntu, you can check this tutorial. Modified 2 years, 6 months ago. Connect and share knowledge within a single location that is structured and easy to search. The difference between both characters is that, the first character, the exclamation sign! Hot Network Questions. Improve this question. At this point, we have a capable binary, su , that has its own PAM config installed.

I can suggest to visit to you a site on which there are many articles on this question.