Vpn wikipedia
View more global usage of this file. This file contains additional information, vpn wikipedia, probably added from the digital camera or scanner used to create or digitize it. If the file has been modified vpn wikipedia its original state, some details may not fully reflect the modified file.
Mobile VPNs are used in environments where workers need to keep application sessions open at all times, throughout the working day, as they connect via various wireless networks, encounter gaps in coverage, or suspend-and-resume their devices to preserve battery life. A conventional VPN cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out, [1] fail, or even the computing device itself to crash. A VPN maintains an authenticated, encrypted tunnel for securely passing data traffic over public networks typically, the Internet. Makers of mobile VPNs draw a distinction between remote access and mobile environments. A remote-access user typically establishes a connection from a fixed endpoint, launches applications that connect to corporate resources as needed, and then logs off. In a mobile environment, the endpoint changes constantly for instance, as users roam between different cellular networks or Wi-Fi access points. A mobile VPN maintains a virtual connection to the application at all times as the endpoint changes, handling the necessary network logins in a manner transparent to the user.
Vpn wikipedia
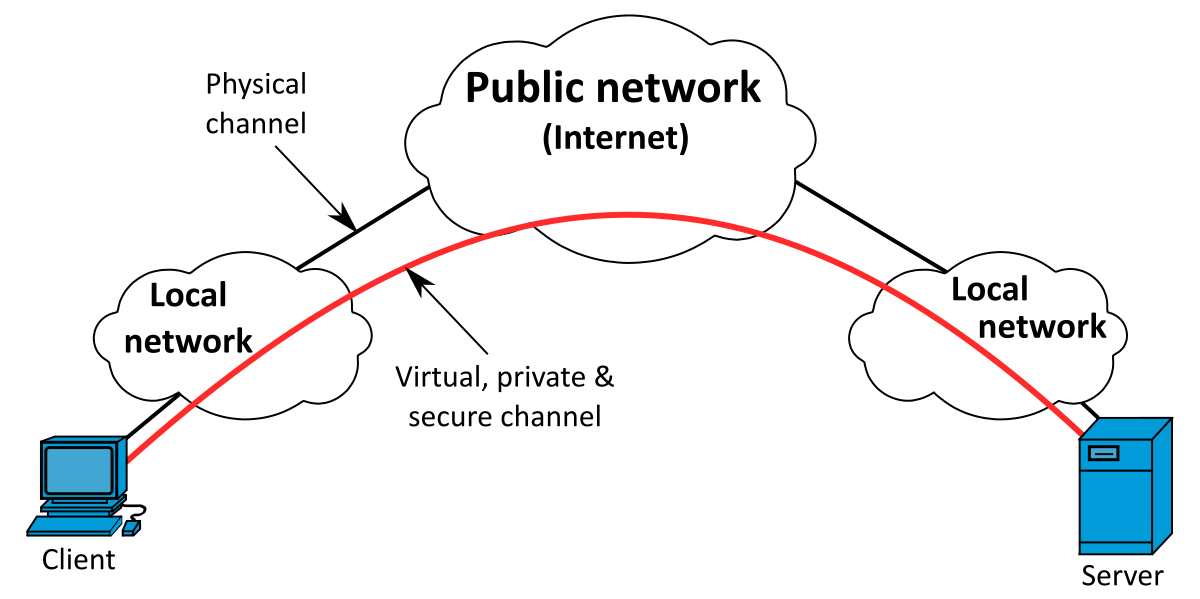
A virtual private network , or VPN is a set of technologies which are used to link computers to create a private network. Another network is used to carry the data, which is encrypted. The carrier network will see the packets of data which it routes. To the users of the VPN, it will look like the computers were directly connected to each other. In a business context, VPNs are often used to connect different office locations or to allow people working from outside the company network to access its resources. VPNs are a crucial tool for securing sensitive data and enabling secure remote access for employees, especially with the rise of remote work. Businesses are turning to VPNs to create a secure and encrypted connection for employees accessing company data from remote locations, ensuring that work websites that cannot be accessed on the normal internet can be securely accessed. Additionally, VPNs provide a safe and encrypted connection for employees to access company resources, protecting sensitive data from cyber threats. Similarly, the encryption process allows VPNs to offer anonymity by hiding the user and making it very hard for anyone to track them. As a result, VPNs help make one's online activities on the web anonymous and undecipherable. VPNs are often used to access websites that are blocked in some countries, like China. VPNs can also be used to connect corporate offices to the larger branch offices, also known as site-to-site VPN. This is because direct network connections are impractical between offices that are physically distant. Contents move to sidebar hide.
How Mullvad handles payment information.
A virtual private network VPN service provides a proxy server to help users bypass Internet censorship such as geoblocking and users who want to protect their communications against data profiling or MitM attacks on hostile networks. A wide variety of entities provide "VPNs" for several purposes. But depending on the provider and the application, they do not always create a true private network. Commercial VPN services are often used by those wishing to disguise or obfuscate their physical location or IP address, typically as a means to evade Internet censorship or geo-blocking. Providers often market VPN services as privacy-enhancing, citing security features, such as encryption, from the underlying VPN technology. However, users must consider that when the transmitted content is not encrypted before entering the proxy, that content is visible at the receiving endpoint usually the VPN service provider's site regardless of whether the VPN tunnel itself is encrypted for the inter-node transport.
The laws of physics suggest wormholes through space and time are hypothetical; but wormholes do exist in cyberspace and wonders can be found on the other side. We call these cyberspace wormholes virtual private network VPN connections. In the diagram below the connection between the branch office and headquarters could be a permanent site to site VPN connection. Home and mobile users are able to create client on-demand VPN connections to the VPN server at the branch office or the headquarters. All internet-connected devices have a local public or private internet protocol IP address eg. When connected using a VPN the device gains access to the network at the other end of the VPN and is provided with an IP address on the remote network, even though it is not physically there.
Vpn wikipedia
A virtual private network , or VPN is a set of technologies which are used to link computers to create a private network. Another network is used to carry the data, which is encrypted. The carrier network will see the packets of data which it routes. To the users of the VPN, it will look like the computers were directly connected to each other. In a business context, VPNs are often used to connect different office locations or to allow people working from outside the company network to access its resources. VPNs are a crucial tool for securing sensitive data and enabling secure remote access for employees, especially with the rise of remote work.
Api routes not working laravel
Yes [82]. Browsing activity In late , companies providing VPN services claimed the Great Firewall of China became able to "learn, discover and block" the encrypted communications methods used by a number of different VPN systems. Retrieved January 24, The world's largest encrypted email service. No [d]. User Experience and Statistics. Select " I accept the terms in the License Agreement " and press the " Install " button. No [35]. Similar responses were found in respondents from other countries as well. Dedicated []. Load to the openvpn client the openvpn-uhem-config. Retrieved August 7, All of our VPN gateways run on dedicated hardware servers.
A virtual private network VPN service provides a proxy server to help users bypass Internet censorship such as geoblocking and users who want to protect their communications against data profiling or MitM attacks on hostile networks. A wide variety of entities provide "VPNs" for several purposes.
No [53]. The audit confirmed that the company's privacy policy was upheld and the no-logging policy was true again. Download as PDF Printable version. Yes [33] [34]. Wired UK. IPv6 Leak Protection. In a positive review published by Tom's Guide in October , the reviewer concluded that "NordVPN is affordable and offers all the features that even the hardcore VPN elitists will find suitable". Multi-platform support. Retrieved September 29, Trusted VPNs do not use cryptographic tunneling; instead, they rely on the security of a single provider's network to protect the traffic. Electronic health records , Electronic medical records , Picture archiving and communications systems , Computerized physician order entry , pharmacy, patient registration, scheduling, housekeeping, billing, accounting. Yes [89].

0 thoughts on “Vpn wikipedia”